Steganography - The Technique
The word steganography is of Greek origin and means "concealed writing" from the Greek words steganos meaning "covered or protected", and graphei meaning "writing”, means covered or secret writing, and is a long-practiced form of hiding information. Steganography's intent is to hide the existence of the message, while cryptography scrambles a message so that it cannot be understood.
More precisely,
Steganography includes a vast array of techniques for hiding messages in a variety of media. Among These methods are invisible inks, microdots, digital signatures, covert channels and spread-spectrum communications. Today, thanks to modern technology, steganography is used on text, images, sound, signals, and more.
KERCKOFF PRINCIPLE
In cryptography: This principle states that “the security of the system has to be based on the assumption that the enemy has full knowledge of the design and implementation details of the steganographic system”. The only missing information for the enemy is a short, easily exchangeable random number sequence, the secret key.
Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. Generally, messages will appear to be something else: images, articles, shopping lists, or some other cover text and, classically, the hidden message may be in invisible ink between the visible lines of a private letter. Steganography includes the concealment of information within computer files. In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. As a simple example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it.
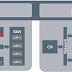
BASIC MODEL
We give some definitions common to the steganography field:
Cover medium: This is the medium in which we want to hide data, it can be an innocent looking piece of information for steganography, or some important medium that must be protected for copyright or integrity reasons.
Embedded message: This is the hidden message we want to put in the cover. It can be some data for steganography and some copyright informations or added content for digital watermarking.
Stegokey: This is represented by some secret information, which is needed in order to extract the embedded message from the stegomedium Stego-medium: This is the final piece of information that the casual observer can see.
We can define this simple formula:
Cover-medium + embedded-message = stego-message
Message is the data that the sender wishes to remain it confidential. It can be plain text, cipher text, the image, or anything that can be embedded in a bit stream such as a copyright mark, a covert communication, or a serial number. Password is known as stego-key, which ensures that only recipient who know the corresponding decoding key will be able to extract the message from a cover-object. The cover-object with the secretly embedded message is then called the Stego-object. Recovering message from a stego-object requires the cover-object itself and a corresponding decoding key if a stego-key was used during the encoding process. The original image may or may not be required in most applications to extract the message.
USES
Legitimate Use
Steganographic techniques have obvious uses, some legitimate, some less so, and some are likely illegal. The business case for protection of property, real and intellectual is strong. The watermarking of digital media is constantly improving, primarily in an attempt to provide hardened watermarks or proof of ownership. Individuals or organizations may decide to place personal/private/sensitive information in steganographic carriers. Admittedly, there are usually better ways to manage this task. One can liken these applications to the use of a deadbolt lock on a door.
Illegal Use
Other uses for
steganography range from the trivial to the abhorrent. There are claims (47)
that
child pornography
may be lurking inside innocent image or sound files. While this is entirelypossible, a search on the internet for confirmation of this claim was unsuccessful.
An annual report on High Technology crime (48) lists nine common types of computer crime:
· Criminal communications
· Fraud· Hacking
· Electronic payments
· Gambling and pornography
· Harassment
· Intellectual property offenses
· Viruses
· Pedophilia
In examining this
list, one can identify several of these areas where steganography could be
used, especially considering the broad term “criminal communications.”
Thanks and Regards,
Amoeba Technologies Core Team | info@amoebatechno.com
www.amoebatechno.com | 24 x 7 Support No: +91-8886516000
Facebook: https://www.facebook.com/AmoebaTechnologies
www.amoebatechno.com | 24 x 7 Support No: +91-8886516000
Facebook: https://www.facebook.com/AmoebaTechnologies






















0 comments :